acme.sh official wiki
You definately need a domain before apply, you can get one at any registars, like name, namecheap, spaceship, gandi …
You can reach tld-list to get promotion codes and compare price among registars.
The detail of how acme protocol validate your domain and sign a certificate may look up here. It primarily validate the control through web and DNS record without human intervention, which is why the service can be free unlike the certificates for signning code.
Install acme.sh
acme.sh is actually a pile of .sh scripts just like its name. You can install it by:
curl https://get.acme.sh | sh -s [email protected]
The email used to create an account with CA(Certificate Authority), which is required in applying certificates. Here, it will automatically create an account with default CA–zerossl, you can remove -s [email protected] to create later and switch to other server you like.
Short name for CA servers, you may change CA like:
acme.sh --set-default-ca --server letsencrypt acme.sh --set-default-ca --server zerossl acme.sh --set-default-ca --server google
creating an account:
acme.sh --register-account -m [email protected]
Notice: this only available for zerossl and let’s encrypt or any other CA do not need extra details.
If you want certificates from GTS(Google Trust Services), look up here. In simply terms, create a project in IAM admin in Console , and obtain EAB key in cloud shell from the web interface by typing this:
gcloud publicca external-account-keys create
Then, using the EAB key to register an account back to your host:
acme.sh --register-account -m "EMAIL" --server google --eab-kid "EAB_KID" --eab-hmac-key "HMAC_KEY"
remember eab-hmac-key is the longer one, and if you want to test out first in a staging platform, you need to obtain another key from gcloud to create another account for staging platform, since the EAB key expired once it used.
Apply with dns_api
Apply through DNS verification does not necessitate physical hosting. Regardless of the server’s physical location or whether there are multiple servers, you can issue certificates for a domain as long as you have control over its DNS records. Demonstrating control over the domain’s DNS records through DNS verification typically signifies enhanced authentication and security measures. Issuing wildcard certificates will necessitate DNS verification. So I prefer validate domain with DNS records.
Here is an example if you add your domain to cloudflare:
We need a special token can change DNS records from.
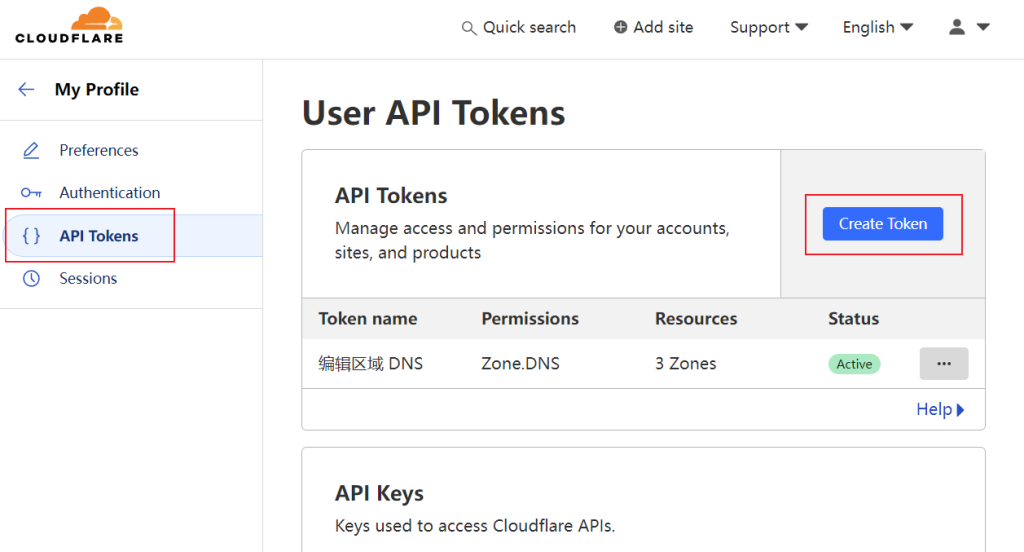
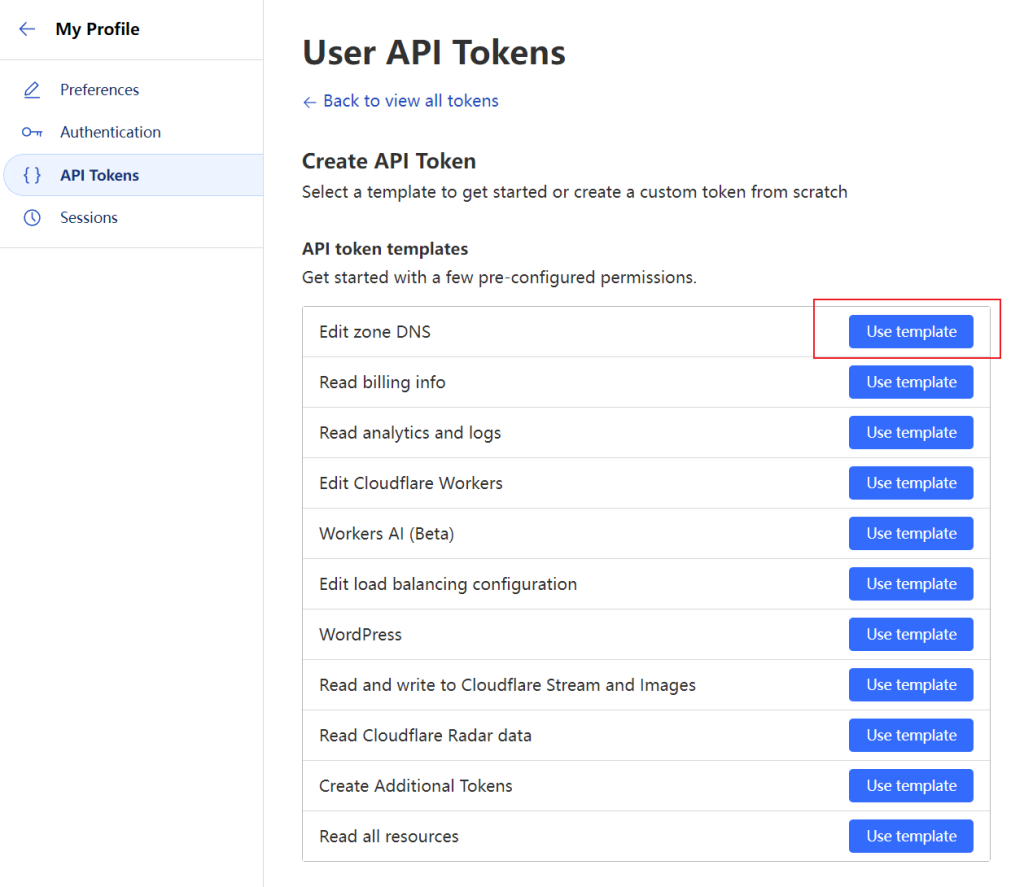
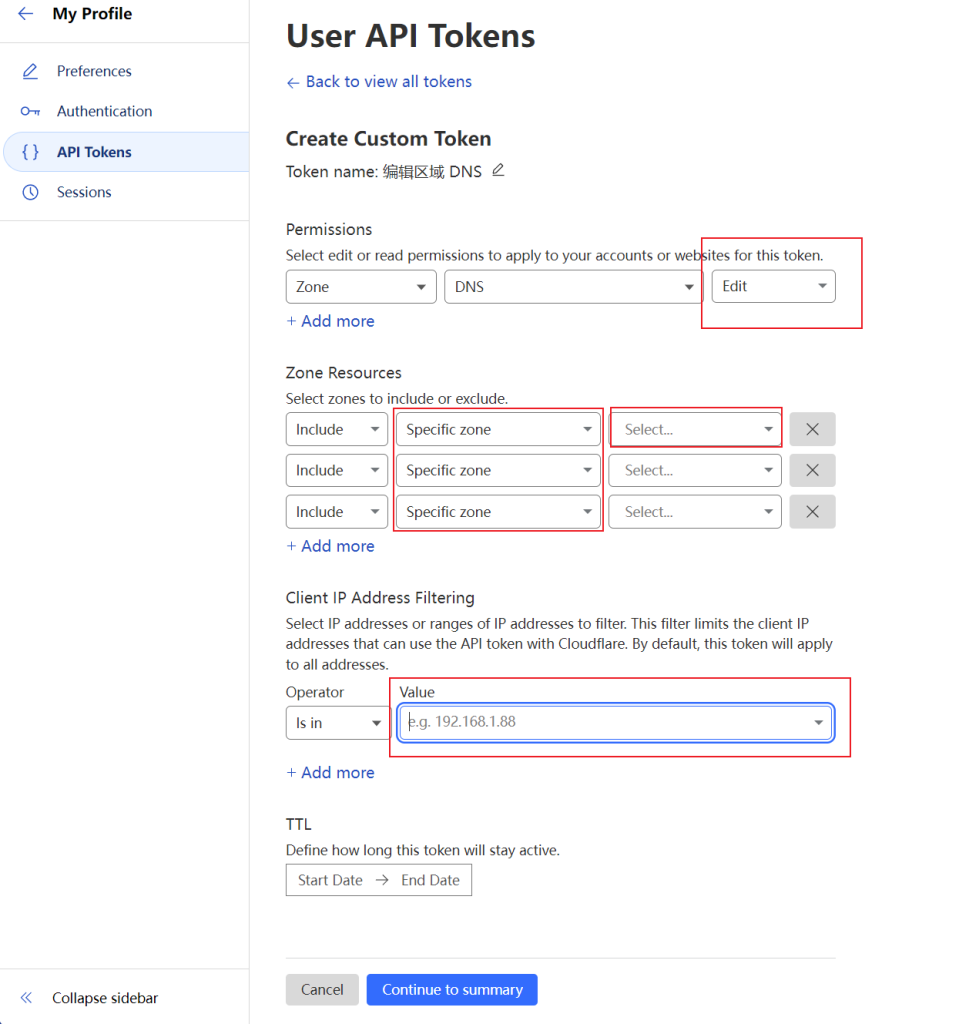
Change the permission to allow edit, and add the domain you want in specific zone, set the IP filter to only allow your host’s IP.
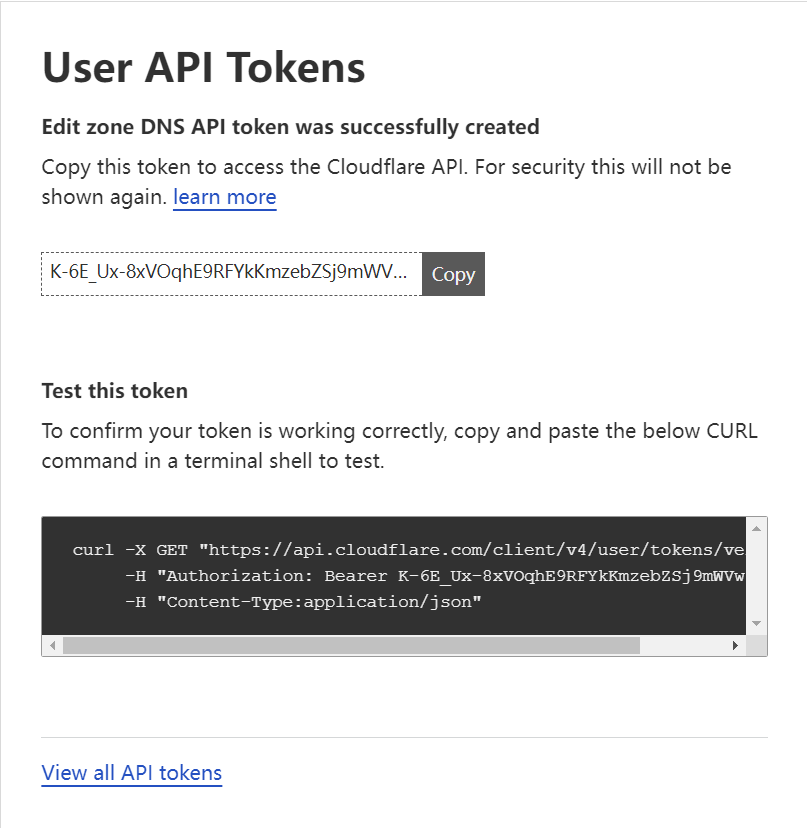
You can test the token first.
And then we can finally apply certificate with this token, replace Your_CF_Token
export CF_Token="Your_CF_Token"
Once this token used for applying certificate, acme.sh will store this token to ~/.acme.sh/acme.sh/account.conf , so you may also add this line to the file:
SAVED_CF_Token='Your_CF_Token'
and then:
acme.sh --issue -d *.domain.tld --dns dns_cf --keylength ec-256 # or as you like acme.sh --issue -d domain.tld --dns dns_cf --keylength ec-384
After successfully receiving your certificate, you can use this command to copy them to wherever you want:
acme.sh --install-cert -d domain.tld \ --cert-file "/path/to/domain.tld.cer" \ --key-file "/path/to/domain.tld.key" \ --fullchain-file "/path/to/domain.tld_fullchain.cer" \ --reloadcmd "sudo service nginx force-reload"